Embedded Wallets: A bird’s eye view
The humble beginning
Ben Reinhart
|Mar 9, 2023

At Privy, we are building the simplest way to onboard all your users to web3, whether they are new to the space or tried-and-true experts. This means building a library that enables developers to meet users where they are, and cater to diverse audiences whose product experiences grow with their engagement.
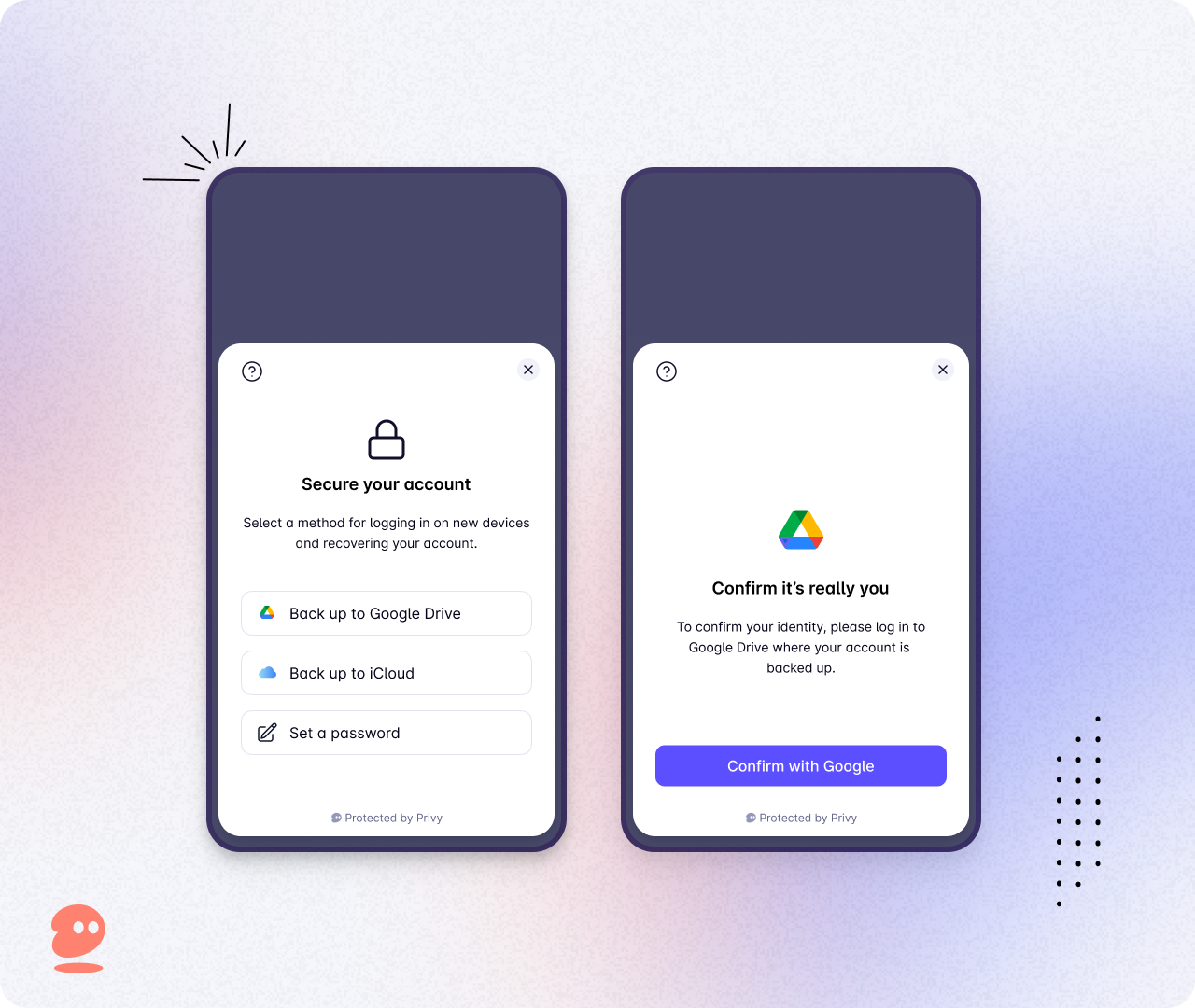
Privy’s embedded wallets allow applications to create fully-functional Ethereum wallets on-demand without requiring users to leave the app. With this feature in place, we believe we are about to unlock a significant UX boost for the Web3 ecosystem!
The space itself is abuzz with changes that will profoundly shape UX, as threshold-based multi party computation matures, and smart contract wallet architectures (often called “account abstraction”) are standardized. While we are extremely excited about these evolutions and are working with partners to bring them into our own product, our core focus is enabling developers to build meaningful end-to-end solutions from day 1. To that end, we wanted this post to share some technical details on how embedded wallets got their start.
In the beginning, there was entropy
A wallet is born when 128 bits of entropy are chosen randomly by a CSPRNG. These bits are converted to a mnemonic via BIP-39 which is used to derive the user’s wallet key pair.
While wallet software is many things, the entirety of the wallet can be reduced to these 128 bits.
The choices are 128, 160, 192, 224, or 256 bits. These map to 12, 15, 18, 21, and 24 word mnemonics. 128 was chosen for its simplicity. This will be configurable by integrating applications.
Sharing is caring
It’s critical the entropy (henceforth referred to as the mnemonic) is secured and only accessible by the end-user it belongs to.
Privy’s embedded wallets achieve this by deploying a Shamir Secret Sharing scheme where the mnemonic is split into N shares and can be recovered using M of N shares. In our implementation, three total shares are allocated, with two belonging to the end-user and one secured by Privy. This has two core advantages: Privy alone cannot reconstruct the mnemonic and access user keys, and the user can always access their keys without needing to go through Privy.
We value our clients
To protect users and remain non-custodial, mnemonics and other plaintext key material are never transmitted over networks or exposed to servers. Everything happens on the end-user’s device. Wallets are created on the end-user’s device. Shares are reconstructed on the end-user’s device. Requests are serviced on — you get it.
Thus, clients are responsible for protecting the user’s wallet. While the UI remains under control of integrating applications, we leverage headless iframes to create a sandboxed environment where keys can safely be used to service requests sent to the wallet.
Compatibility is key
We value interoperability and choice. Users must be able to take their wallet keys with them in the event they no longer wish to use Privy.
Like all modern wallets, embedded wallets are Hierarchical Deterministic Wallets and adhere to the multi-account hierarchy specified in BIP-44. This ensures compatibility across existing wallet software and thus enables users to switch clients at any time with the click of a button.
User experience is paramount
Private keys and mnemonics are not particularly human-friendly, especially for non-technical users. Therefore, it is imperative that Privy shield users from the technical underpinnings. To the extent possible, Privy creates a Web2-like experience with features your every day user would expect. Examples include social logins, cross-device support, and simple account recovery.
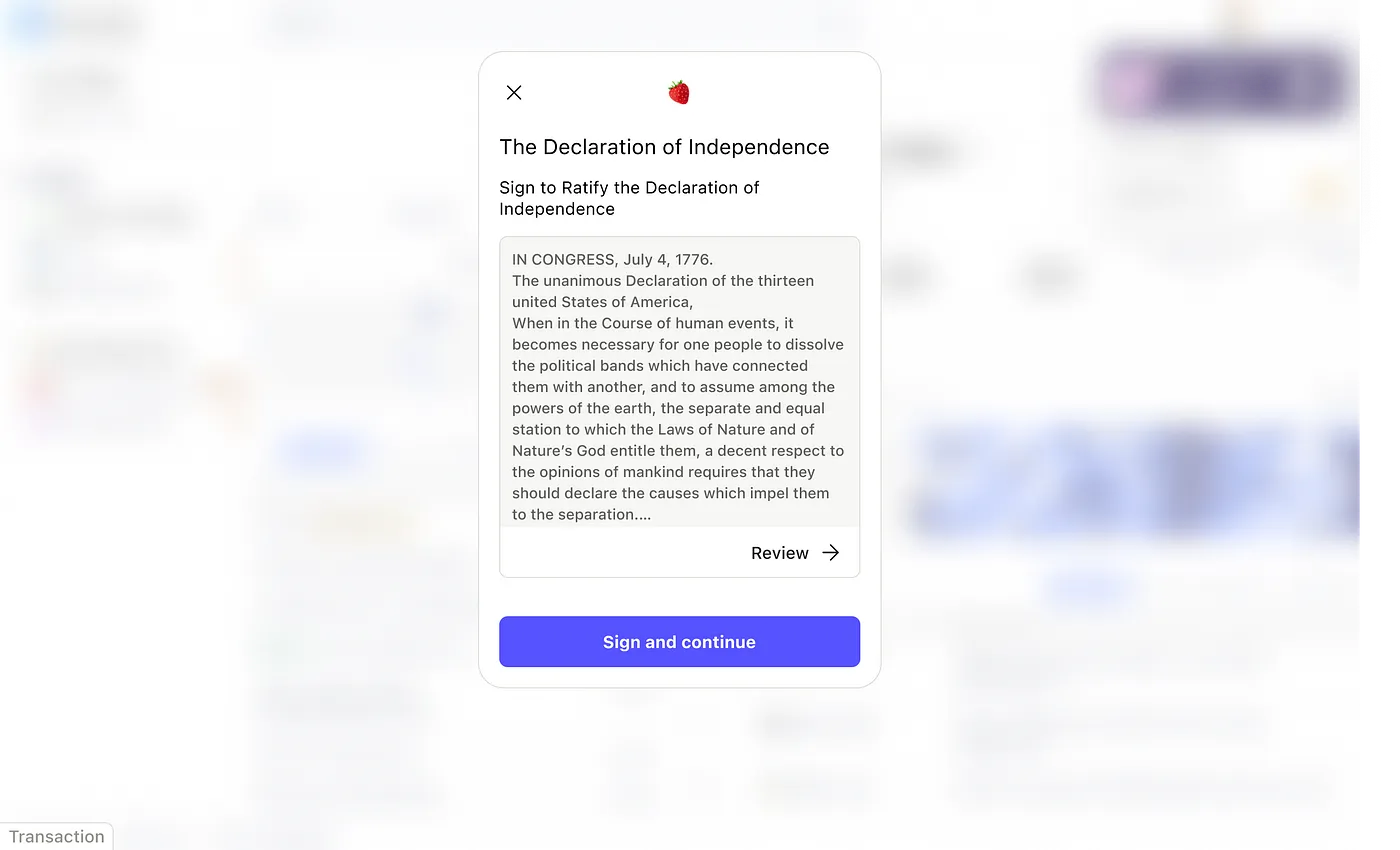
One feature to highlight here is enabling developers to craft human-readable messages for their users. This enables signature and transaction requests to be on-brand and contextually relevant.
Looking ahead
Enabling users to come in with their existing wallet, or create one on the fly for app usage unlocks new possibilities in web3. Building for diverse audiences is essential to driving web3 forward all while maintaining that which makes the space exciting: ownership, interoperability and composability of data and assets.
We believe embedded wallets are going to be huge. Even though we’re just getting started, we’re excited about various improvements across the UX, DX, and the overall security of these wallets. If this sounds like a feature that would give your app a boost, we’d love to help get you started!