Powering programmable wallets with low-level key management
How Privy’s low-level APIs let you build programmable treasuries with policies, key quorums, and webhooks.
Debbie Soon
|Nov 10, 2025

Every onchain action, be it a signature or a transaction, begins with a key. It’s the invisible layer that governs trust, access, and control.
Privy’s wallet infrastructure starts at that layer, giving developers full control over how deeply they want to build. Teams can start from low-level APIs that expose the same primitives our infrastructure uses internally, or use higher-level SDKs and out-of-the-box UIs that abstract those details away.
Key management at Privy is thus highly programmable, letting developers decide what policies govern a wallet’s behavior, and what it can sign. From bare metal to whitelabel flows, it’s all the same foundation: secure by design, modular by default.
How Privy handles key management
When a user creates a wallet, Privy provisions and manages their key securely within Trusted Execution Environments (TEEs). These are isolated, hardware-protected environments that prevent anyone, including Privy, from accessing the data or code inside.
Each wallet’s private key is generated inside a TEE and split into two shares:
an enclave share, secured by the TEE and only accessible within it, and
an auth share, encrypted and stored by Privy, retrievable only with valid user authentication.
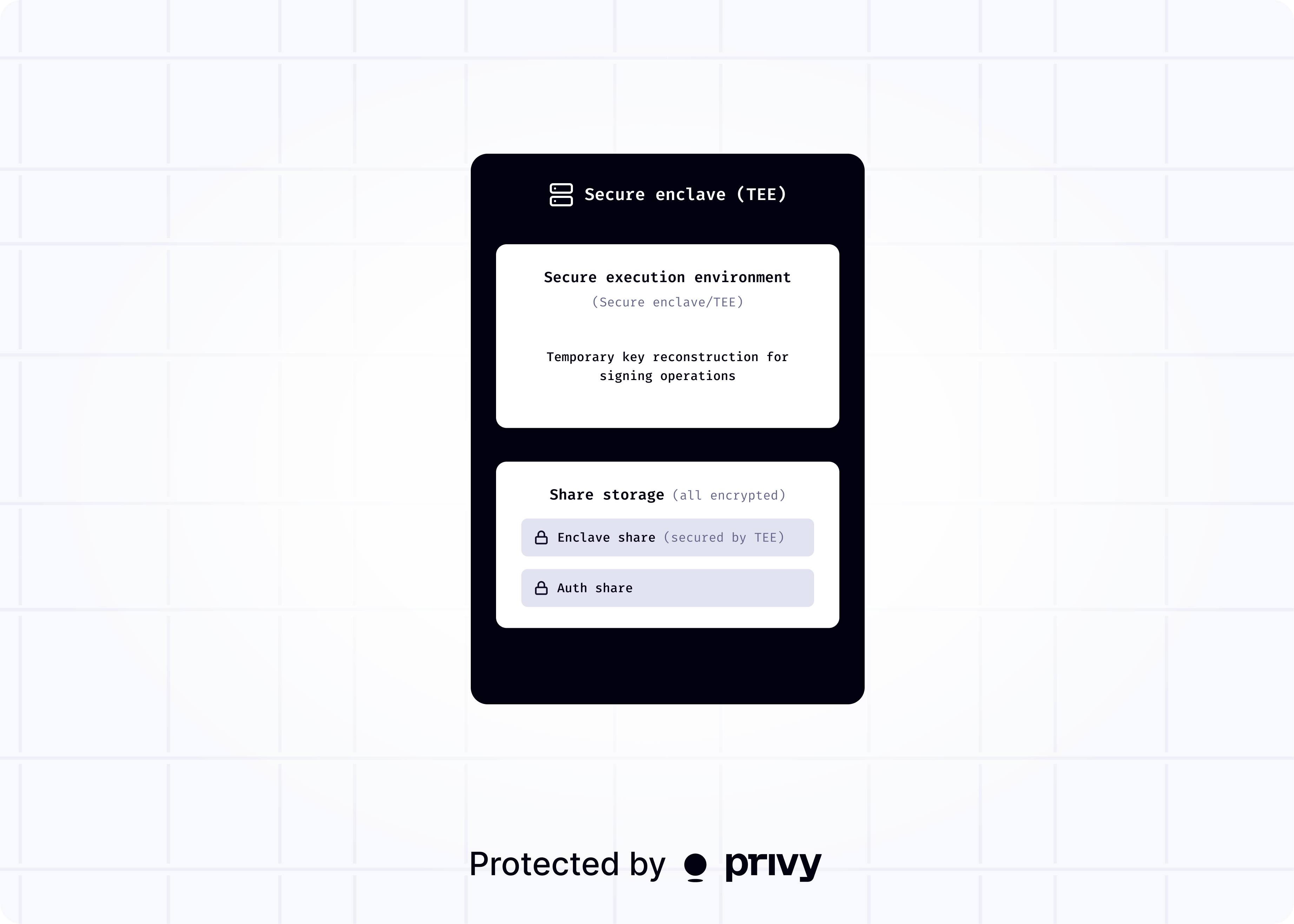
Together they form a 2-of-2 share set, meaning both are required to reconstruct the key and produce a signature. The full key is never persisted and exists only momentarily inside the enclave for signing.
When a user initiates a transaction, Privy verifies authentication before reconstructing the key inside the enclave. The key signs the transaction, is immediately wiped, and cannot be exported.
User custody is cryptographically enforced. Only authenticated users can trigger signing, ensuring wallets remain fully under their control.
This TEE-based architecture provides the foundation for programmable custody — secure, modular, and exposed through low-level APIs that developers can extend and control.
Making wallets programmable with Privy’s low-level key management
Privy’s APIs give developers direct control over the key layer, enabling wallets that are dynamic, context-aware, and governed by policy.
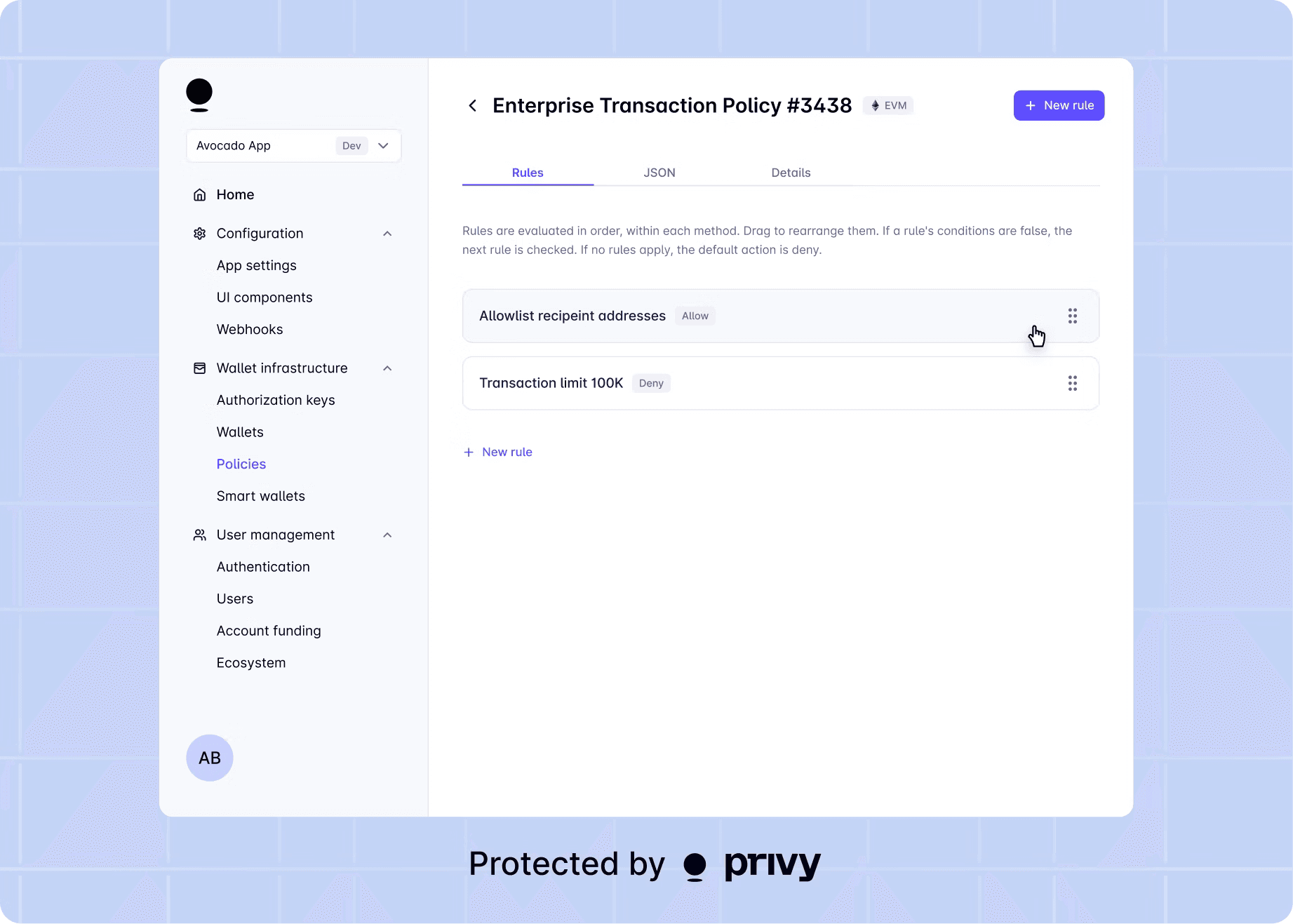
Policy-enforced signing
Low-level key management means that wallets are not just static vaults, and are instead programmable objects.
Developers can write rules that execute inside the enclave before any transaction is signed. For example:
Only sign transactions to approved contracts or chains.
Require user re-authentication above certain thresholds.
Enforce daily spend limits or pause signing dynamically.
Privy’s policy engine enforces rules before any transaction is signed, defining exactly what a wallet can do. These policies turn keys into intelligent security primitives, enforced at the key layer and governed by code.
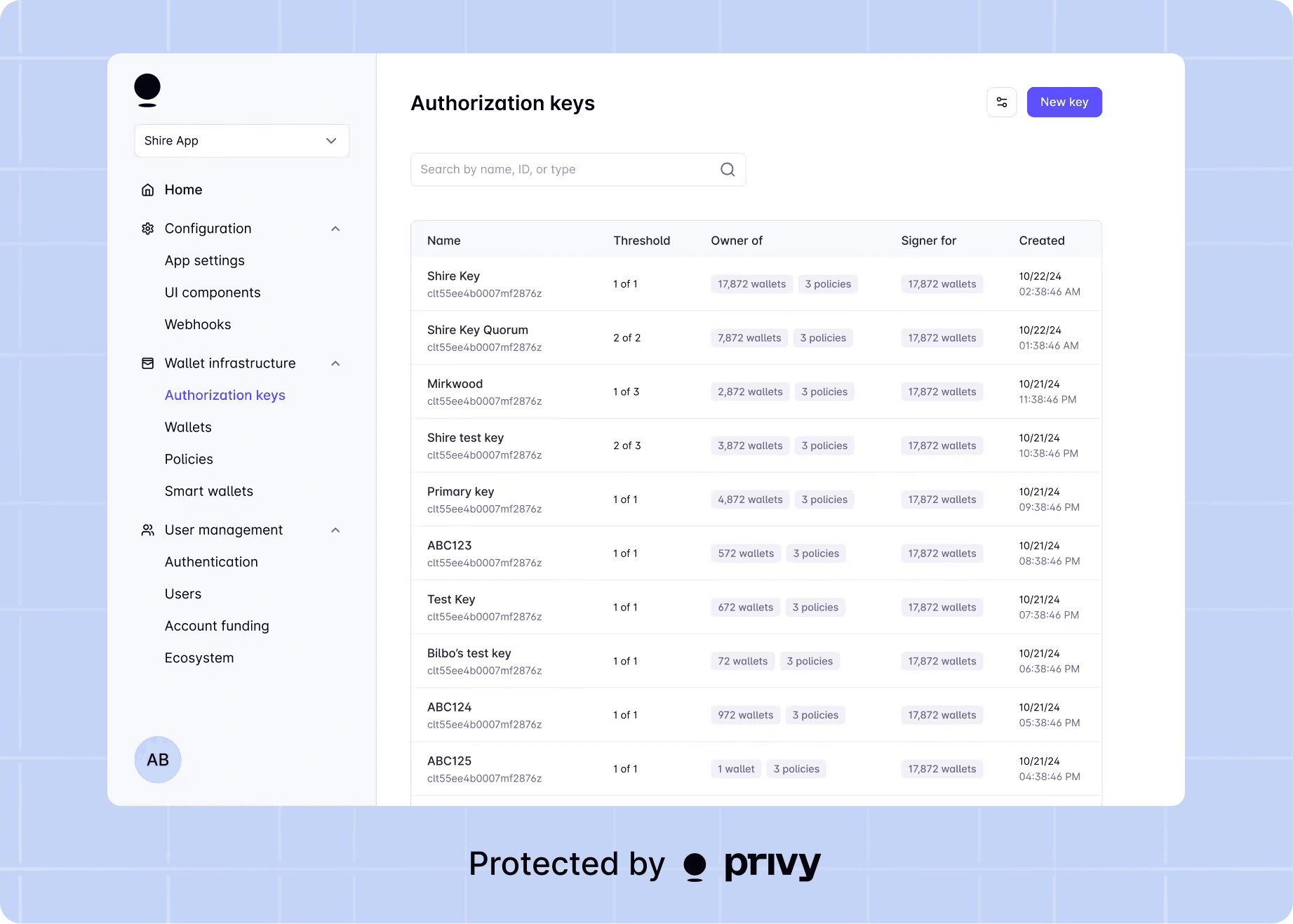
Key quorums
Privy keys can be distributed across multiple enclaves or participants, each holding a fragment of key material.
Developers can then specify quorum thresholds, e.g., 2-of-3 or 3-of-5, that are required to authorize any signature.
This enables:
Multi-sig wallets and shared custody across teams.
Enterprise approval flows for stablecoin transfers or treasuries.
Hybrid models where users and platforms share signing authority.
Quorums are enforced at the key layer, not in application code or smart contracts, which makes them tamper-resistant and chain-agnostic.
Event streaming and webhooks
Every key operation and onchain event within Privy, be it a signature request, policy check, transaction broadcast, or deposit, emits a verifiable update.
Developers can subscribe to these updates through webhooks or fetch them via API to monitor wallet activity in real time.
Common use cases include:
Approval workflows and compliance triggers.
Real-time analytics and transaction monitoring.
Auditable trails for regulated operations.
Privy handles the logic of chain indexing and state management under the hood, keeping your app in sync with deposits, withdrawals, and transaction confirmations across networks.
This makes custody not only secure, but observable and transparent, and a continuous event stream showing how wallets behave and interact onchain.
Why key management matters
Modern treasuries are moving onchain, unlocking speed, transparency, and global reach. With that shift comes a need for programmable control and the ability to move funds quickly while enforcing security and approvals at scale.
Privy’s programmable key management makes this possible.
With Privy, every treasury wallet can enforce rules, approvals, and limits directly at the key layer. Developers can define exactly how funds move and who can authorize them, without relying on external custody or smart contract workarounds.
Here’s what that looks like in practice:
Granular control: Define policies that restrict transactions by recipient, amount, or contract type.
Shared custody: Require signatures from multiple parties before executing large transfers.
Automation: Streamline payouts, settlements, or sweeps through verified onchain actions.
Auditability: Emit events for every signature and policy check, providing verifiable logs for compliance.
These capabilities give teams institutional-grade security with seamless operations, where approvals and automation are built directly into the key layer.
Treasury management is just one of many use cases unlocked by low-level key management. From enterprise operations to consumer wallets, programmable custody allows any app to design security, control, and automation directly into the foundation of its product.
Programmable custody with Privy
Privy’s low-level APIs make it easy to bring programmable custody into your product, from treasuries and wallets to new onchain experiences that haven’t been built yet.
Start exploring Privy's full set of capabilities here.

